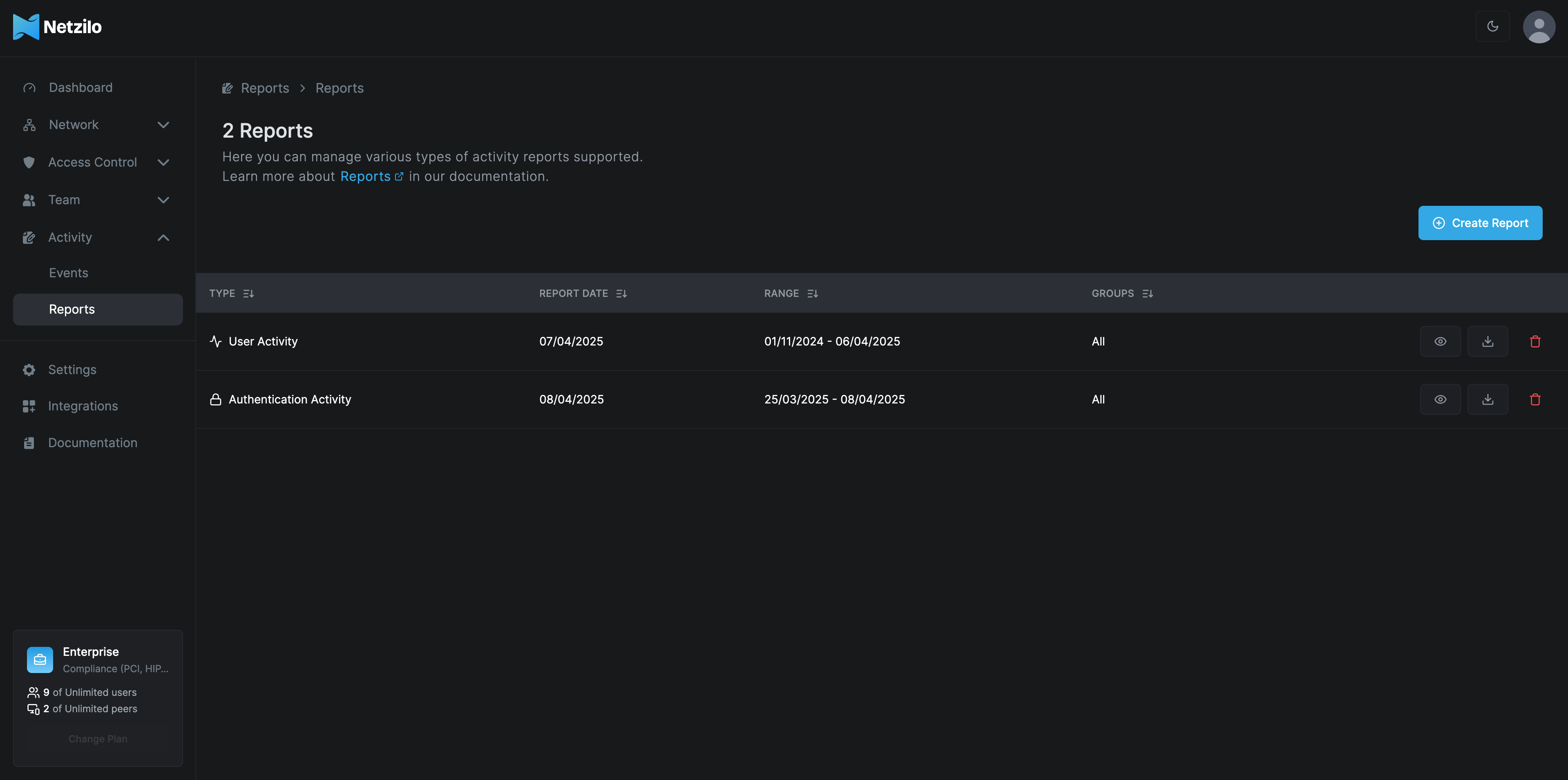
Reports on User and Authentication Activities
The Reports section in Netzilo provides administrators with detailed insights into user and authentication activities. Here, you can:
- View existing reports.
- Download reports for offline analysis.
- Delete outdated or unnecessary reports.
Each report lists the following:
- Type: The type of activity (e.g., User Activity, Authentication Activity).
- Report Date: When the report was created.
- Range: The date range covered by the report.
- Groups: The user groups included in the report.
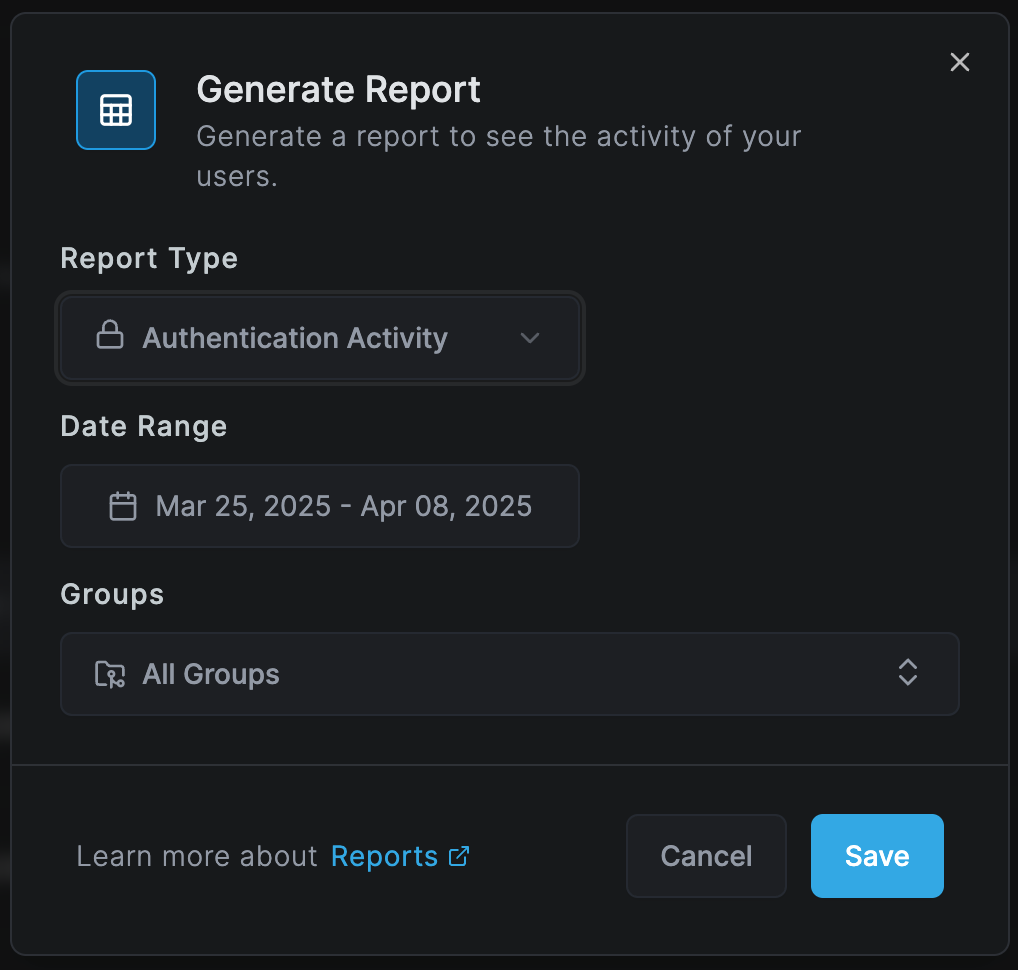
Creating a new report
To generate a new report:
- Click Create Report.
- Select the Report Type (e.g., Authentication Activity).
- Choose a Date Range for the report.
- Select the Groups to include or choose "All Groups".
- Click Save to generate the report.
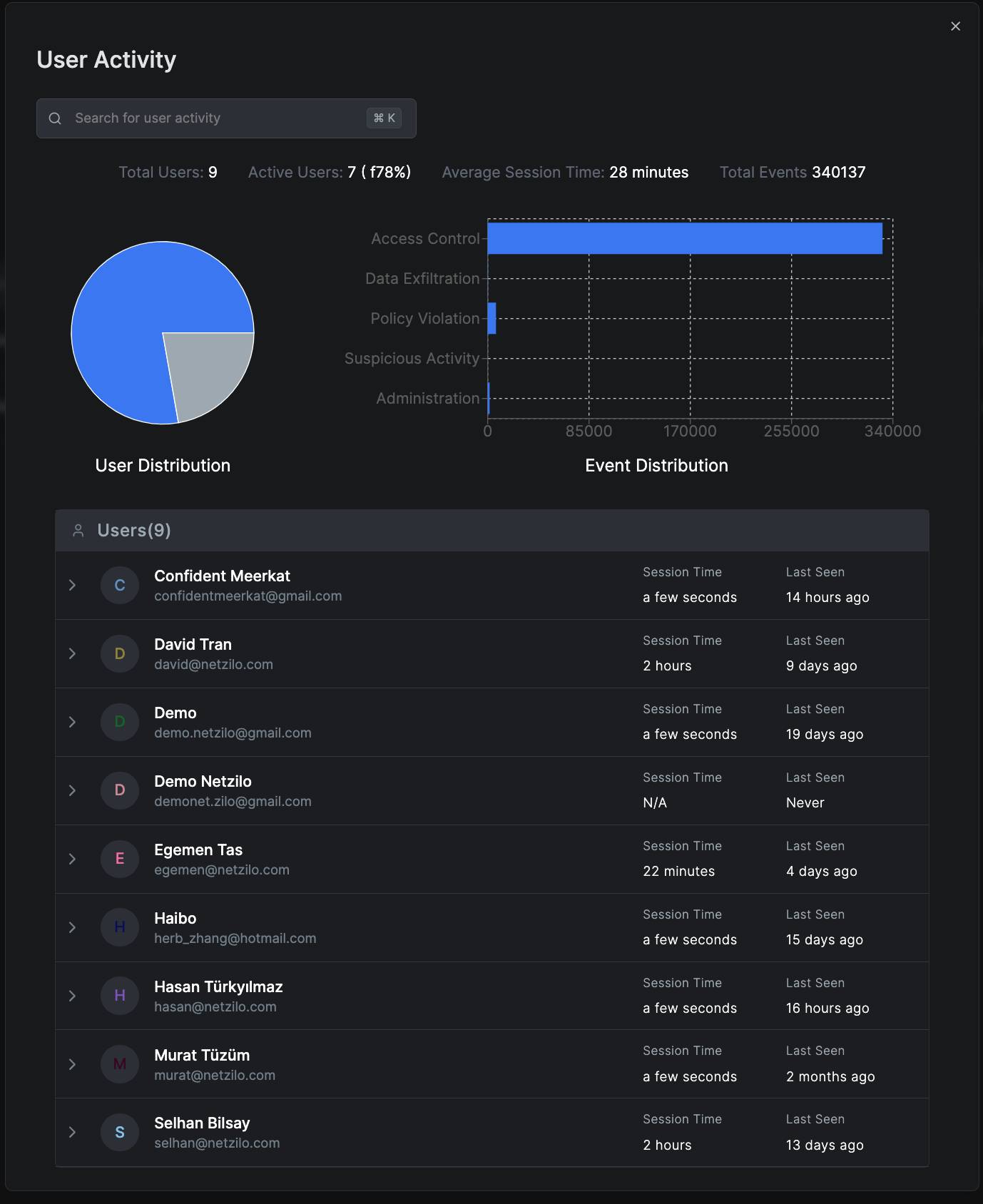
User activity report
Provides in-depth insights into user interactions within Netzilo:
- User Distribution: Shows active versus inactive users.
- Event Distribution: Highlights the types of events, such as Access Control, Data Exfiltration, Policy Violations, Suspicious Activity, and Administration actions.
- Average Session Time: Indicates how long users typically stay active.
- Total Events: Counts all user-generated events.
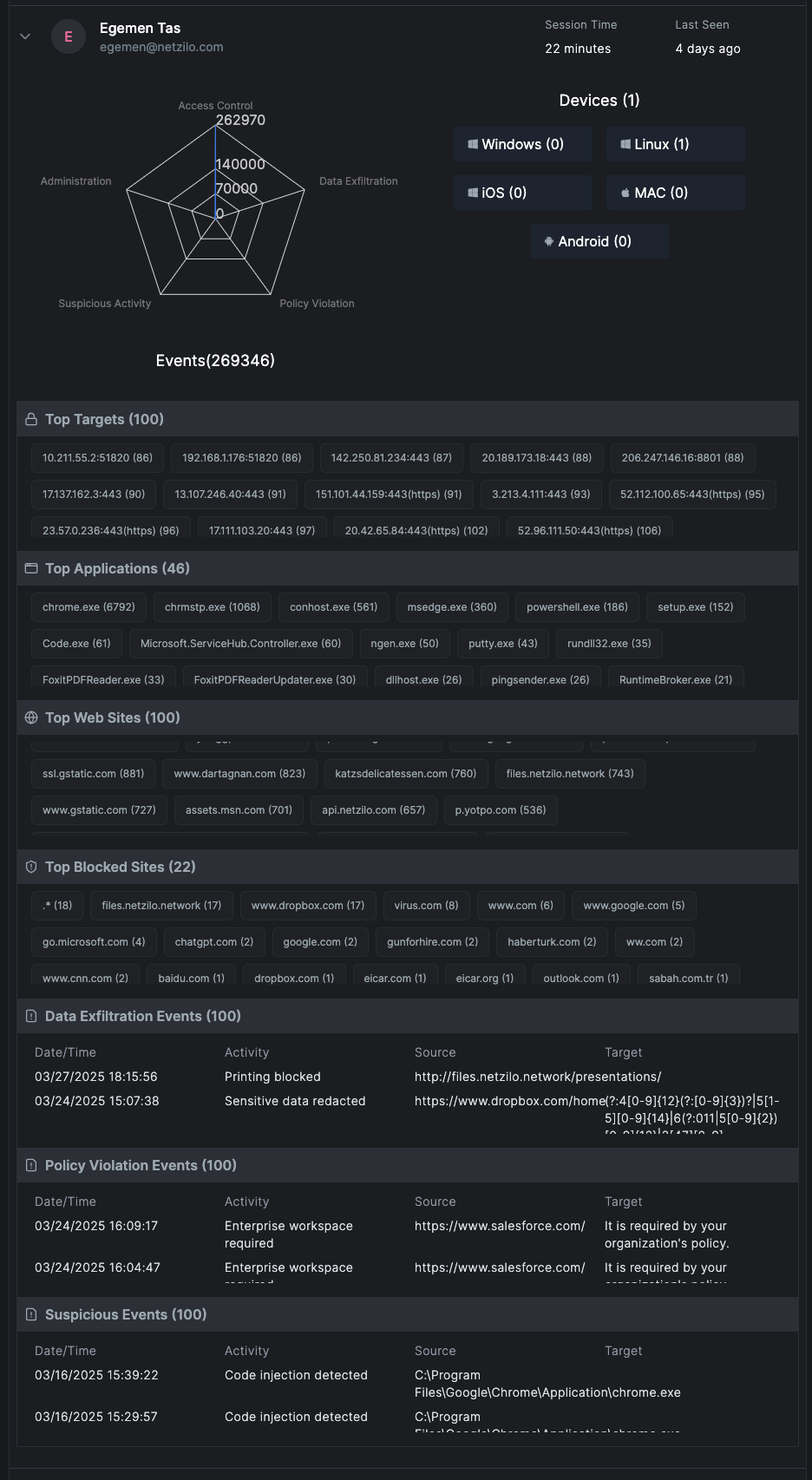
Detailed User Analysis
By clicking on a user, you'll see:
- Event Radar: Visualizes event types and frequencies.
- Device Types: Lists operating systems used by the user.
- Top Targets: Most accessed network targets.
- Top Applications: Most frequently used applications.
- Top Websites: Frequently visited websites
- Top Blocked Sites: Websites that have been blocked.
- Data Exfiltration Events: Details of prevented data leaks.
- Policy Violation Events: Instances where policy compliance was enforced.
- Suspicious Events: Alerts for potentially harmful activities.
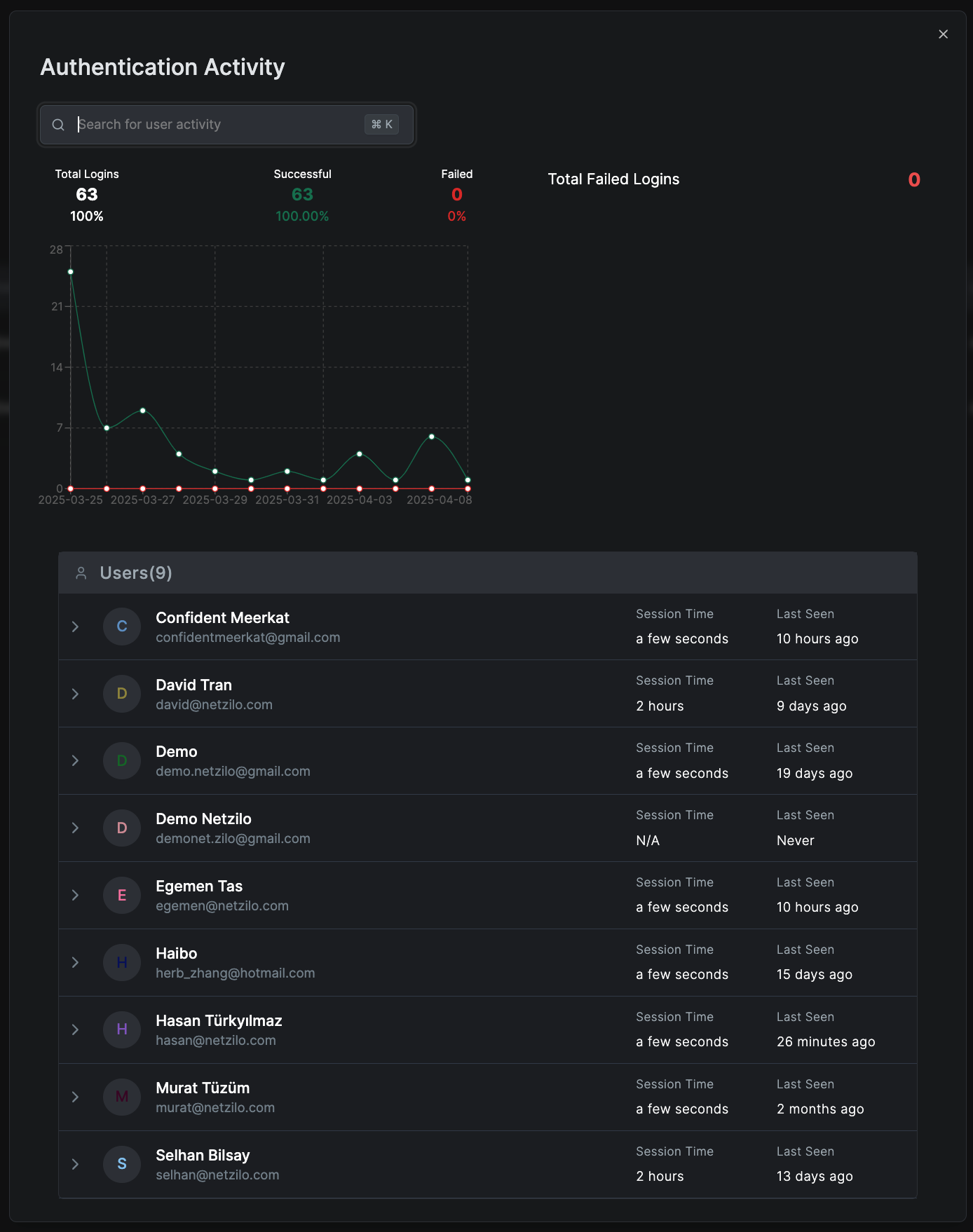
Authentication activity report
This report tracks user login activities. It displays:
- Total Logins: Number and percentage of successful versus failed logins.
- Login Trends Graph: Shows successful and failed login attempts over the selected period.
- Detailed User Login Activity: Lists each user's login statistics, including session durations and last login times. Click on a user to view specific login timestamps.
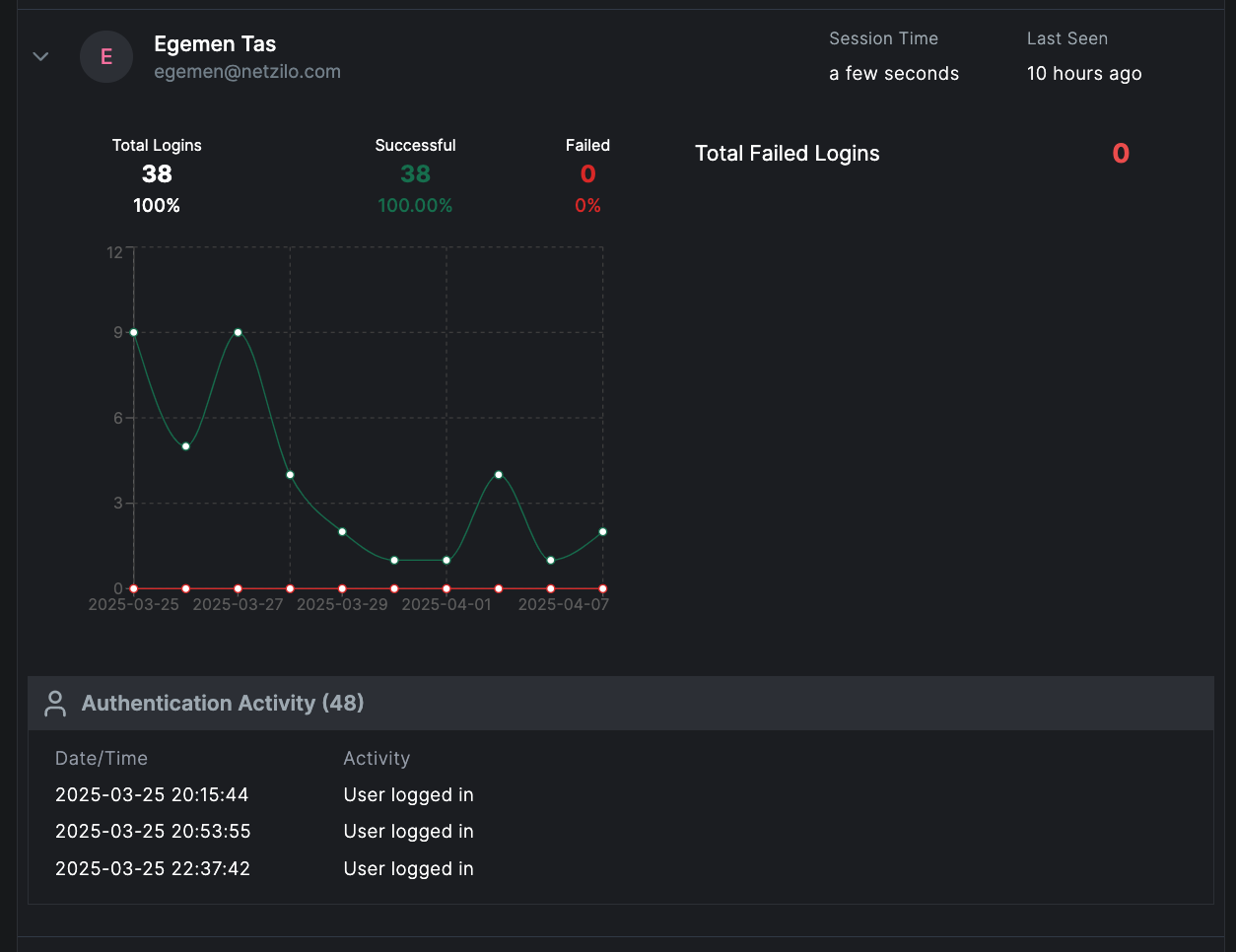
Detailed Authentication Analysis
When you click on a user, you can view:
- Individual Login Trends Graph: Shows login activity for that user across the selected time frame.
- Detailed Authentication Events: A timestamped list of successful and failed login attempts, enabling deeper analysis of user access patterns.
Practical Use
Regularly review these reports to:
- Monitor and analyze user behaviors.
- Ensure compliance with company policies.
- Detect potential security risks early.
- Maintain operational oversight and efficiency.
This section empowers administrators to stay informed and proactive, ensuring optimal security and operational performance within Netzilo.
- Follow us on Linkedin
- Join our Slack Channel

